There are two types of Cloud - public and private. The public ones such as Azure, AWS, Google Cloud Platform have what’s considered a multi-tenant infrastructure, meaning multiple different clients can access the same cloud infrastructure and they share the resources that the cloud provides, however, each client’s data is kept completely separate, like at a bank.
A private cloud is a single-tenant infrastructure, in this case the cloud’s resources are only offered to one organization. A Virtual Private Cloud, or a VPC, is that same concept but inside a public cloud utilising the scalability and ease of use of a public cloud with the data isolation and security of a private cloud.
VPC
In AWS, the VPC service is the networking layer for computing resources and it is free, however, you will be charged normal rates for resources provisioned within the VPC or specific VPC components like traffic mirroring, reachability analyzer or NAT Gateway(s).
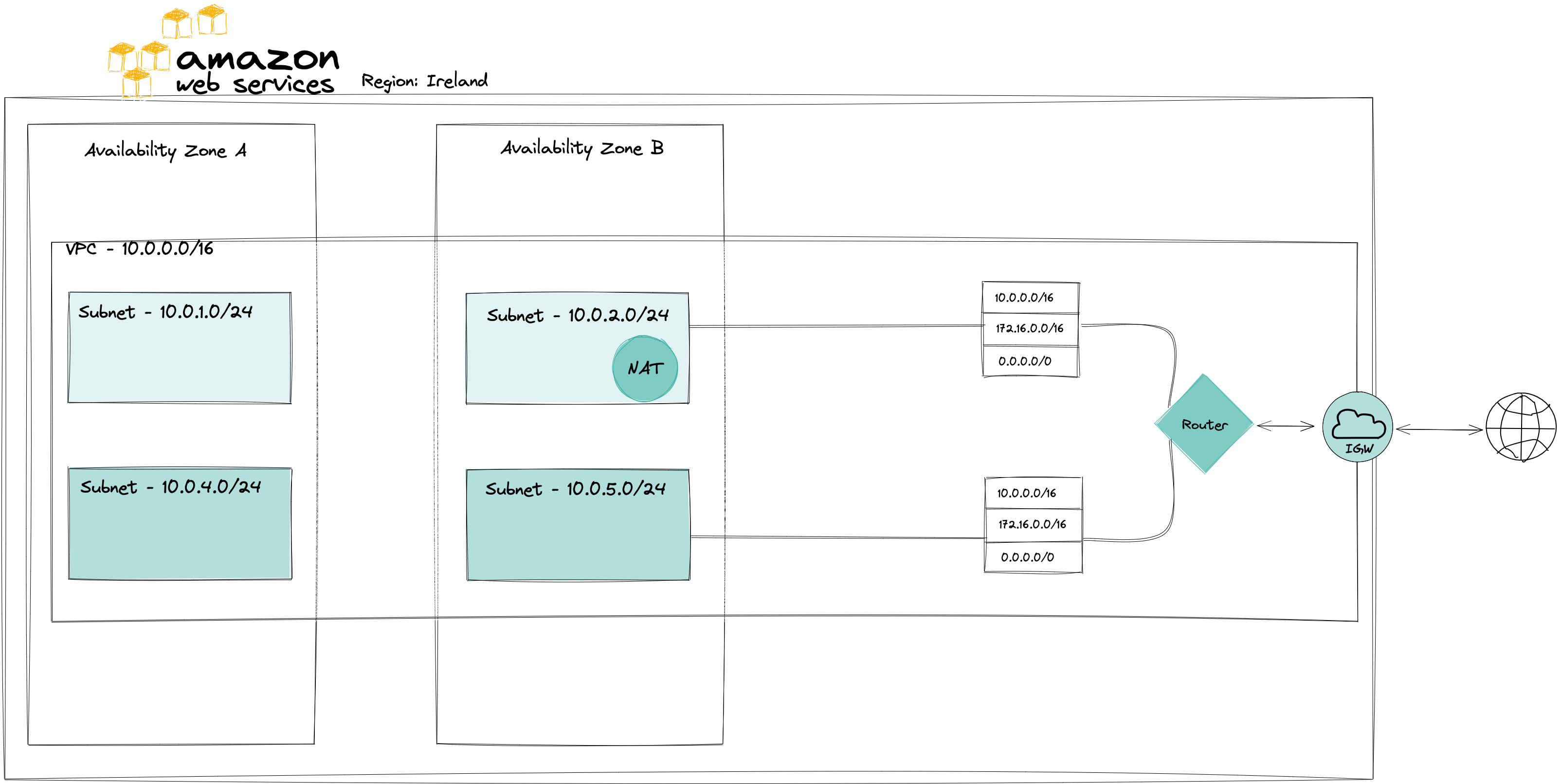
Every VPC requires subnets and routing tables. Depending on business requirements you might also need an Internet Gateway for internet access and a NAT Gateway for a one-way outbound connection with outside resources.
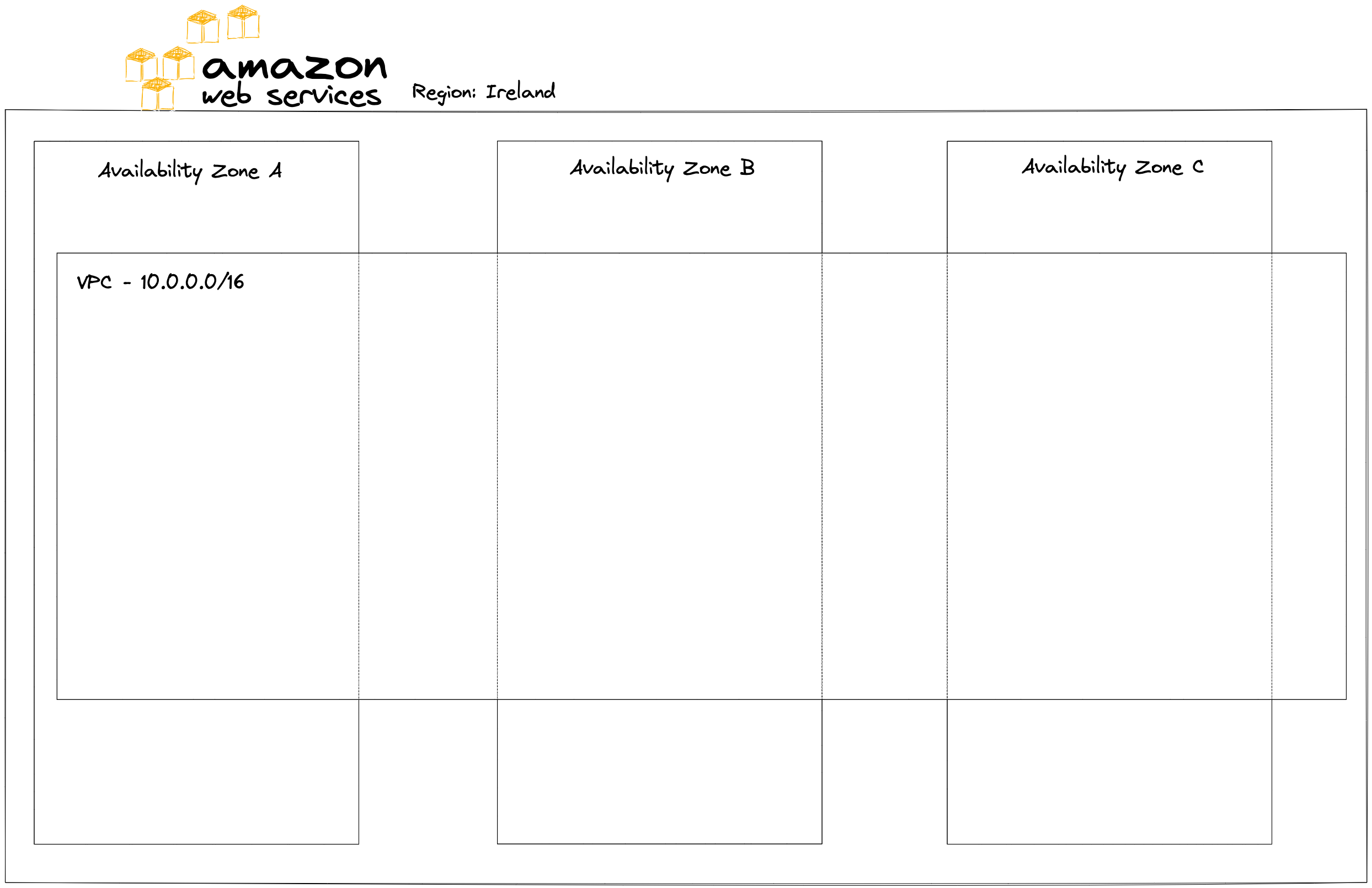
The VPC service is region scoped, which means that it spans an entire region and all its availability zones, however, if we’d like to have a multi-region infrastructure, we’d need to setup VPC peering connection.
With Amazon’s VPC service we can define an entire virtual network with complete control over IP address ranges, subnets, route tables and gateway. This allows us to create a secure and isolated environment for our application’s virtual servers. By default, all new VPCs are completely isolated from outside resources including public internet.
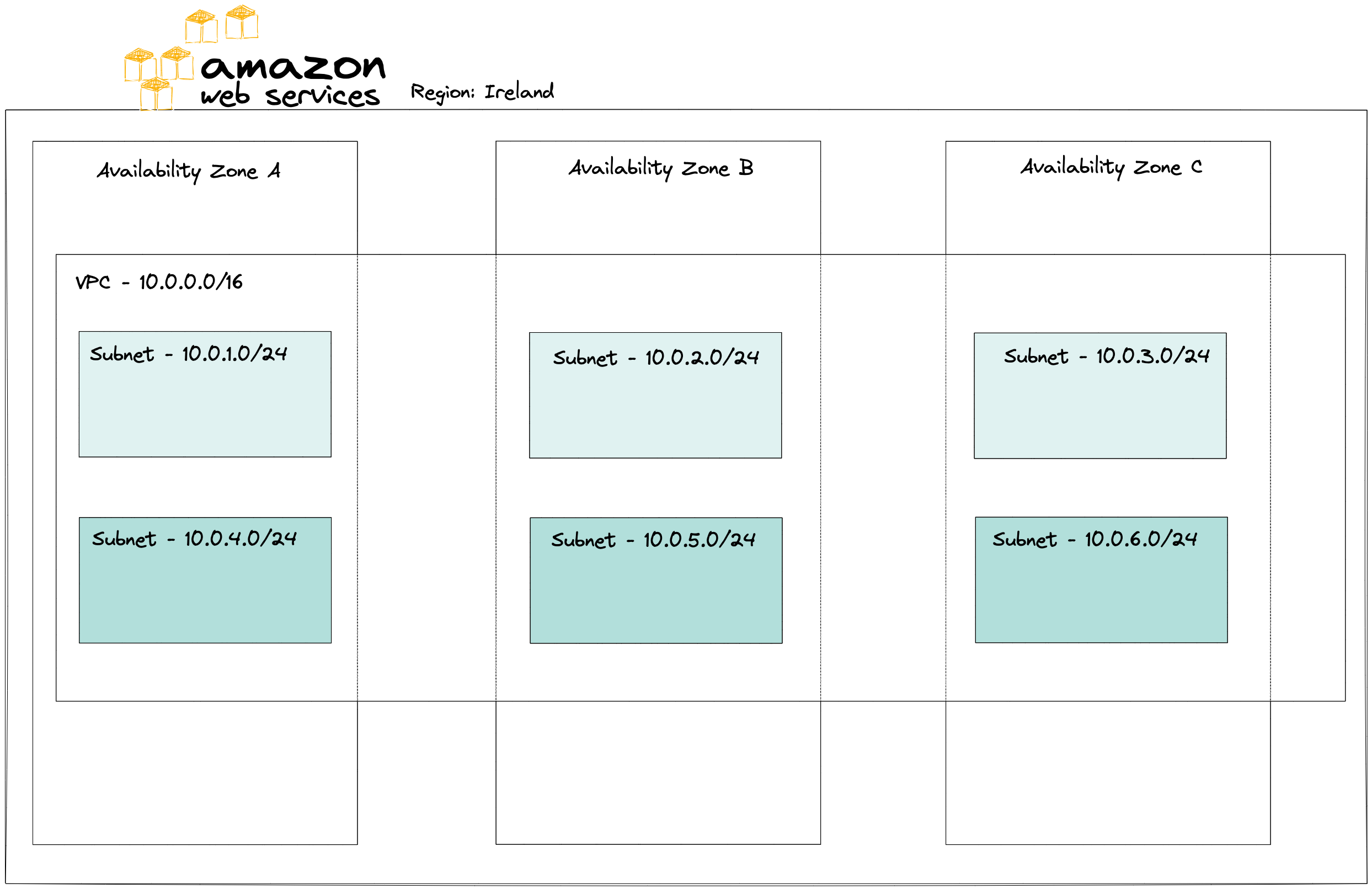
 When creating a new VPC network, we need to define what set of private IP addresses we want to use for the instances within the network. These addresses are specified by providing a CIDR block, e.g. 10.0.0.0/16, we can define blocks anywhere between /16, over 65k addresses, and /28, 16 addresses. The number after the slash specifies how many bits of the IP address will be fixed. In the case of a /16 block, it means that two octets are fixed and two octets are changeable. Each IPv4 address is made up of four octets separated by a dot.
When creating a new VPC network, we need to define what set of private IP addresses we want to use for the instances within the network. These addresses are specified by providing a CIDR block, e.g. 10.0.0.0/16, we can define blocks anywhere between /16, over 65k addresses, and /28, 16 addresses. The number after the slash specifies how many bits of the IP address will be fixed. In the case of a /16 block, it means that two octets are fixed and two octets are changeable. Each IPv4 address is made up of four octets separated by a dot.
Subnets
A subnet is an integral part of the VPC network. They are smaller networks within the VPC and allow us to send requests directly to their destination which ensures higher efficiency of the network. Good visualization of this for me is a neighbourhood (VPC) with apartment buildings, it would be hard to find the right door but luckily there are numbers (subnets) distinguishing the buildings from one another so that it isn’t so difficult.
Subnets do not cost anything and generally the more subnets the better as that provides us with better isolation of resources.
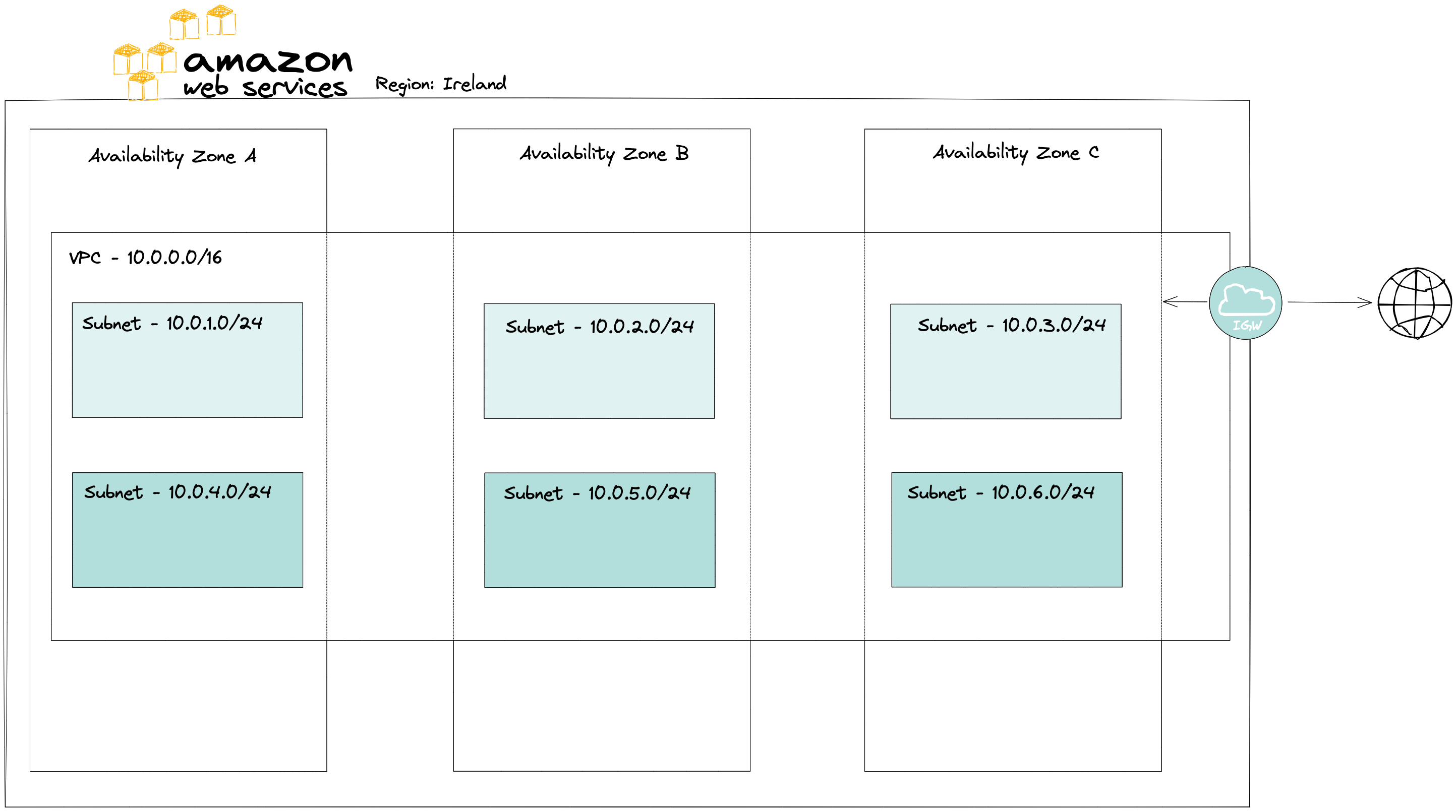
Just like with the cloud itself, there are public and private subnets. They are also often referred to as top - public, and bottom - private, see diagram. The difference between them is that a public subnet will have a rule connecting it with the Internet Gateway. In a private subnet, that connection either will not be allowed or there will be a NAT Gateway rule that will provide only a one-way connection, so that outside resources still cannot send data to the private subnet but can receive data from it.
All our resources will reside within a subnet whether it’s an EC2 virtual server, a database or a data cache. All those resources need an IP address that is within the containing subnet’s IP address range the same way all subnets have to be within the VPC’s IP address range.
Unlike VPCs, that are scoped to an entire region, subnets span only a single availability zone. In the spirit of High Availability it is best to have subnets in at least two different availability zones to provide fail-over.
If a service does not need to be accessed by the public, it is considered a good practice to put it in a private subnet. One of such services would be a Database, the fact that private subnets do not have internet access makes the database much more secure than if it was in a public subnet.
Internet Gateway
Internet Gateway, IGW for short, is a VPC component responsible for routing traffic outside of the private network. Each VPC may have only one Internet Gateway and it cannot be detached while there are IP addresses associated with it. A subnet with IGW access is considered a public subnet.
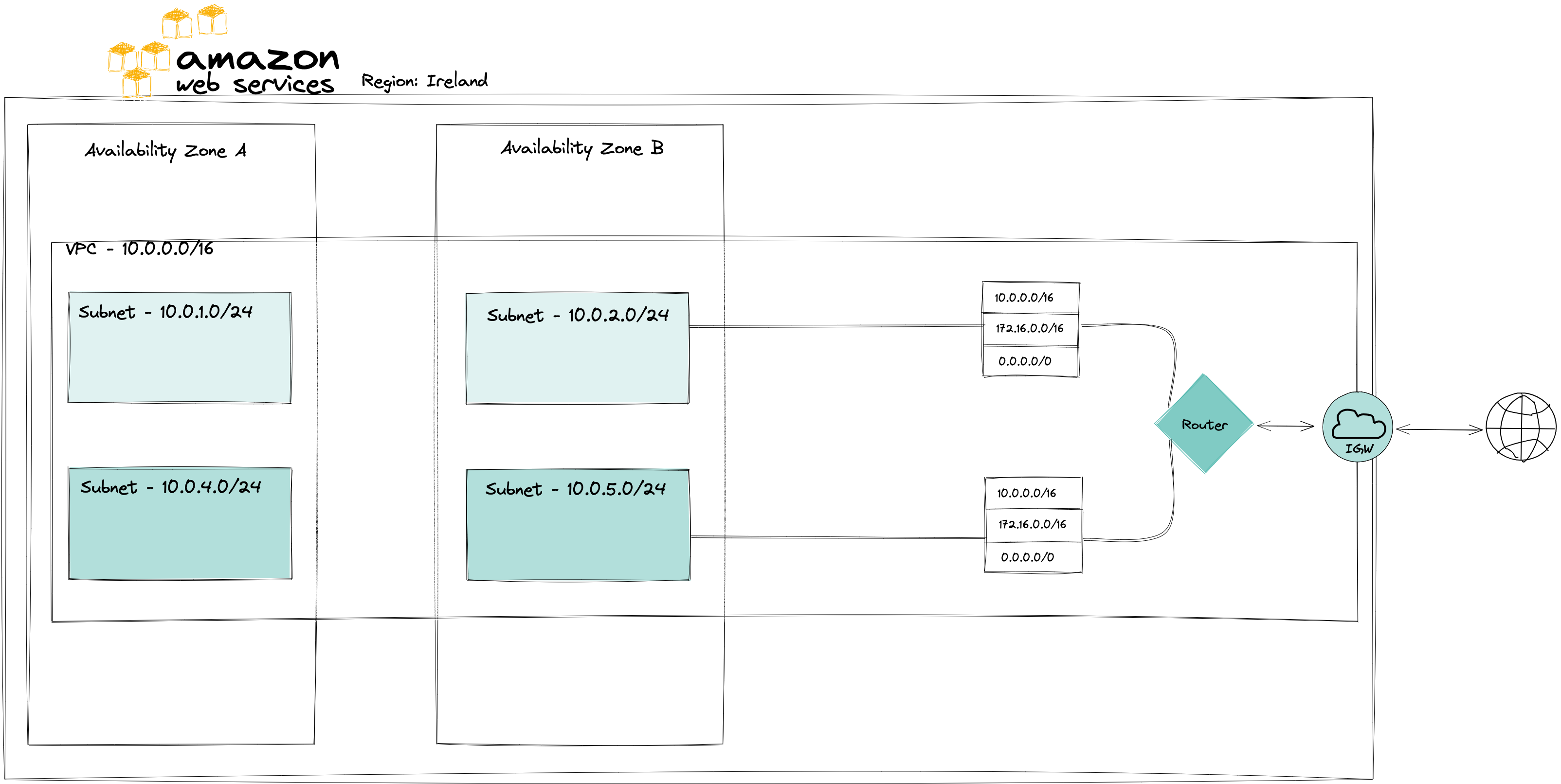
Route Tables
Every VPC has an implicit router and route tables contain rules, or routes, used to control where network traffic is directed. Every subnet needs to be associated with a Route Table but one Route Table can be associated with many Subnets. If a Subnet is not associated with any Route Table it will be implicitly associated with the Main Route Table
Routes are made up of a destination and target. Destination defines where a request is directed, it can be an IP address or a resource ID which represents the range of addresses used by the service. A target is where to send the request next. Almost as if we were flying to London which is the destination, but needed to have a layover in Berlin - target, so we’re going to London via Berlin.
Similar with Route Tables, we can go to CIDR block 0.0.0.0/0 via the Internet Gateway.
Having multiple routes within a Route Table, it depends on the specificity of the CIDR Block which route will be chosen. For example, 0.0.0.0/0 is less specific than 172.34.10.14/32
NAT Gateway
NAT Gateway is a Network Address Translation service. It can be used to provide instances in a private subnet with access to resources outside of the VPC while at the same time those services still cannot establish a connection with those resources. It’s a one way connection.
There are two types of NAT Gateways, public and private. Resources within a private subnet can connect to the Internet via a public NAT Gateway with an Elastic IP Address. Public NAT Gateway must reside within a public subnet as the traffic will be routed through the NAT Gateway to the Internet Gateway.
Private NAT Gateways are used to allow connections to other VPCs or on-premises network for resources within a private subnet. Private gateways cannot have an Elastic IP Address associated with them. It is possible to attach an Internet Gateway to a VPC with a private NAT Gateway, however, if traffic is routed from the NAT Gateway to the Internet Gateway, IGW will drop the traffic.
NACL
NACL, or a Network Access Control List, sometimes also referred to as Network ACL is a layer of security controlling traffic in and out of subnet(s). Each Subnet can be associated with one NACL, however, a single NACL can be associated with many Subnets.
NACL decides which inbound and outbound traffic to allow or deny based on the rule number, evaluated from lowest to highest. The first rule that applies to the traffic type is executed regardless of the rules that come after it with a higher rule number.
Default Network ACL will allow all inbound and outbound http traffic and deny everything else but when creating a new custom NACL, it will deny all traffic until configured otherwise.
So, whereas Route Tables tell the traffic how to get to their destination, a NACL determines whether or not they can get “past the gate” into or out of the subnet.
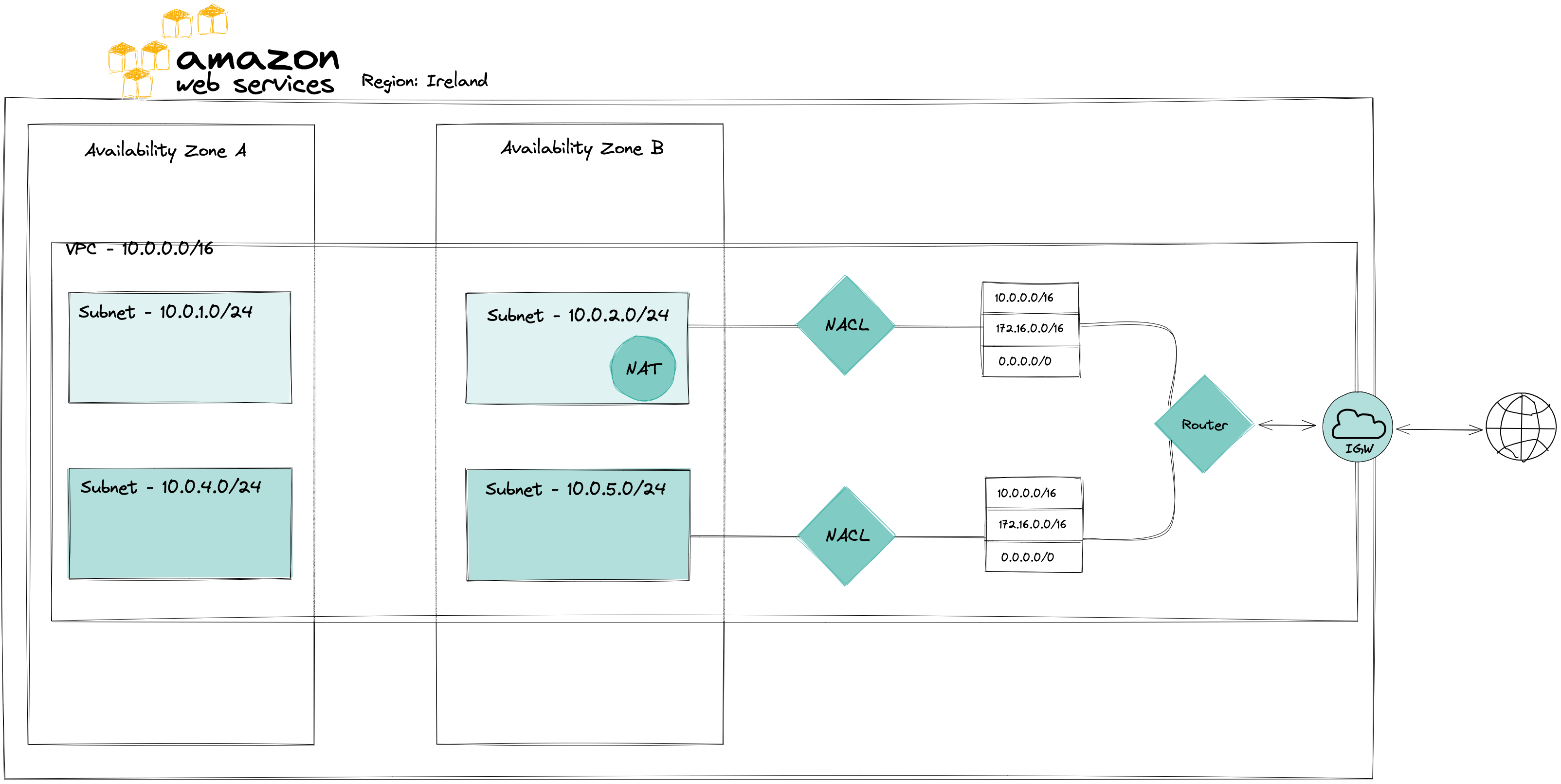
Summary
To sum up, a VPC is our own private network within the public cloud. It is separated from outside resources which we can connect to by adding an Internet Gateway to the VPC. All instances are started within subnets which are smaller networks within the private network. Thanks to the Route Tables we can create rules on how to get to particular resources within the VPC or how to establish a connection with outside resources utilising different Gateways. A NAT instance can be created inside a public subnet in order to provide private subnets with a one-way connection with outside resources - we can send data out but will not accept data coming in. Last but not least, a NACL acts as a firewall, deciding what traffic can enter or leave a subnet.